Your Expectation Goes Beyond the Vulnscan?
Stay Here.
We refine Penetration Testing with precision and transparency. Our certified security experts, via our platform, penetrate all of your assets.
Instant pricing and swift online purchasing allow you to easily initiate an in-depth, non-automated pentest.
Trusted by
Continuous Improvement
With over 15 years of experience and endorsements from global companies, Enfoa’s expertise is proven. Enfoa’s advanced platform and ethical hackers are backed by internationally recognized certifications and challenging training.





Certification & Training
CXO and Tech Friendly Reports
Human Approach
Penetration Testing can’t be automated. While tools can automate some parts, real Penetration Testing requires a highly skilled team to conduct simulated attacks on the network or application, ensuring these attacks are ethical and do no harm.






Zero-Day Vulnerability Researchers
Non-Automated Solutions for Security
Penetration Testing for Compliance
Compliance with various industry standards and regulations is mandatory to protect sensitive information.
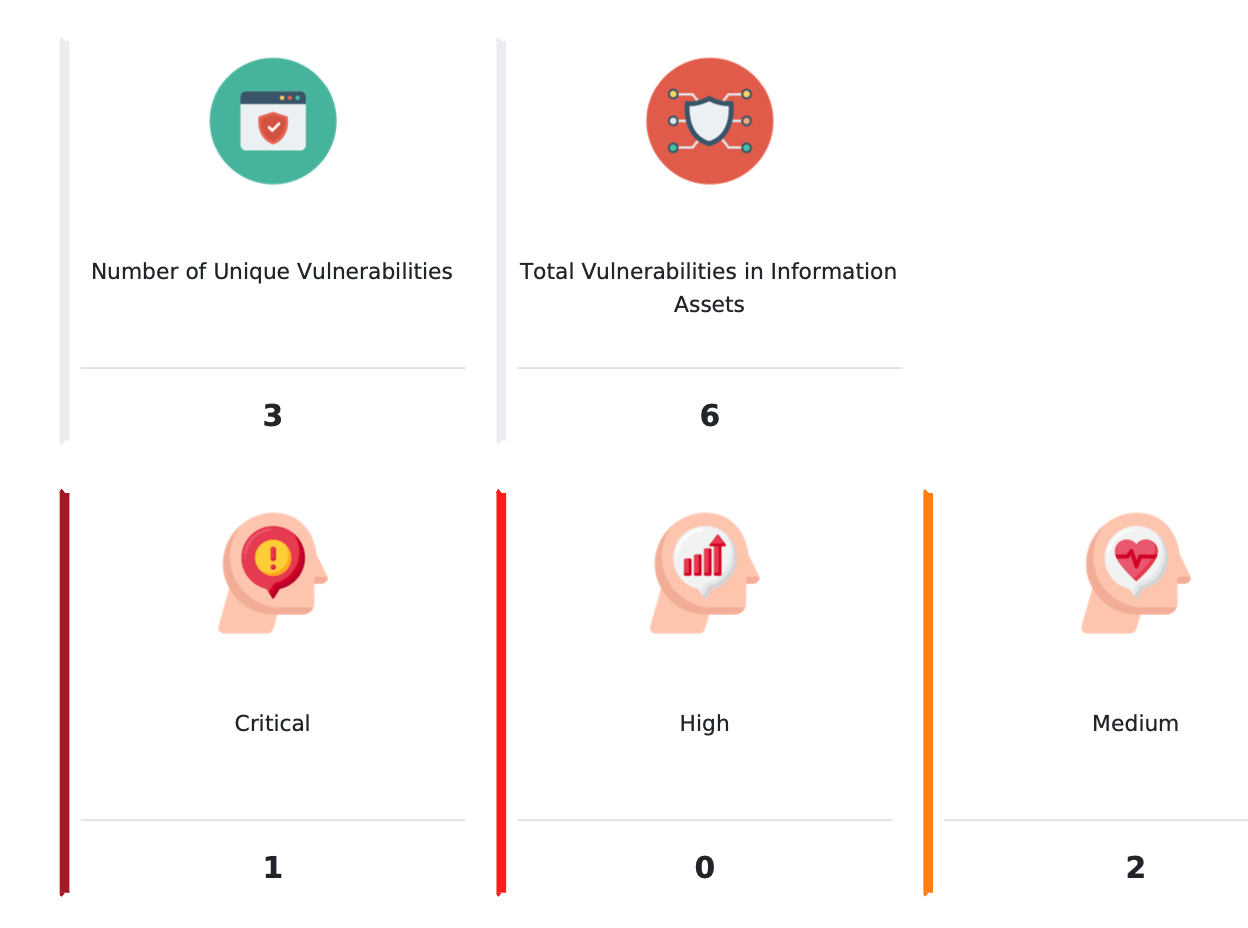
Penetration Testing is critical for assessing security infrastructure vulnerabilities and ensuring compliance with regulations like ISO/IEC 27001, PCI DSS, HIPAA, SOC 1/2, CCPA, GDPR, cyber insurance and more.
Testing of Your Entire Attack Surface
Proactively mitigate risks in real-time with advanced security testing from the top talents in Penetration Testing. Enhance your security team with on-demand access to expert professionals.
Robust platform and extensive experience enable you to efficiently test security controls across your entire attack surface. This approach ensures smarter remediation and improved security outcomes.
Hackers Don't Care About Excuses
Our AI-powered threat detection did not flag it Our DevSecOps pipeline detected nothing The automated pentest found nothing Our machine learning model assessed it as low risk Our bug bounty program has not reported it Our predictive threat intelligence did not forecast this
Comparison Table
Frequently Asked Questions
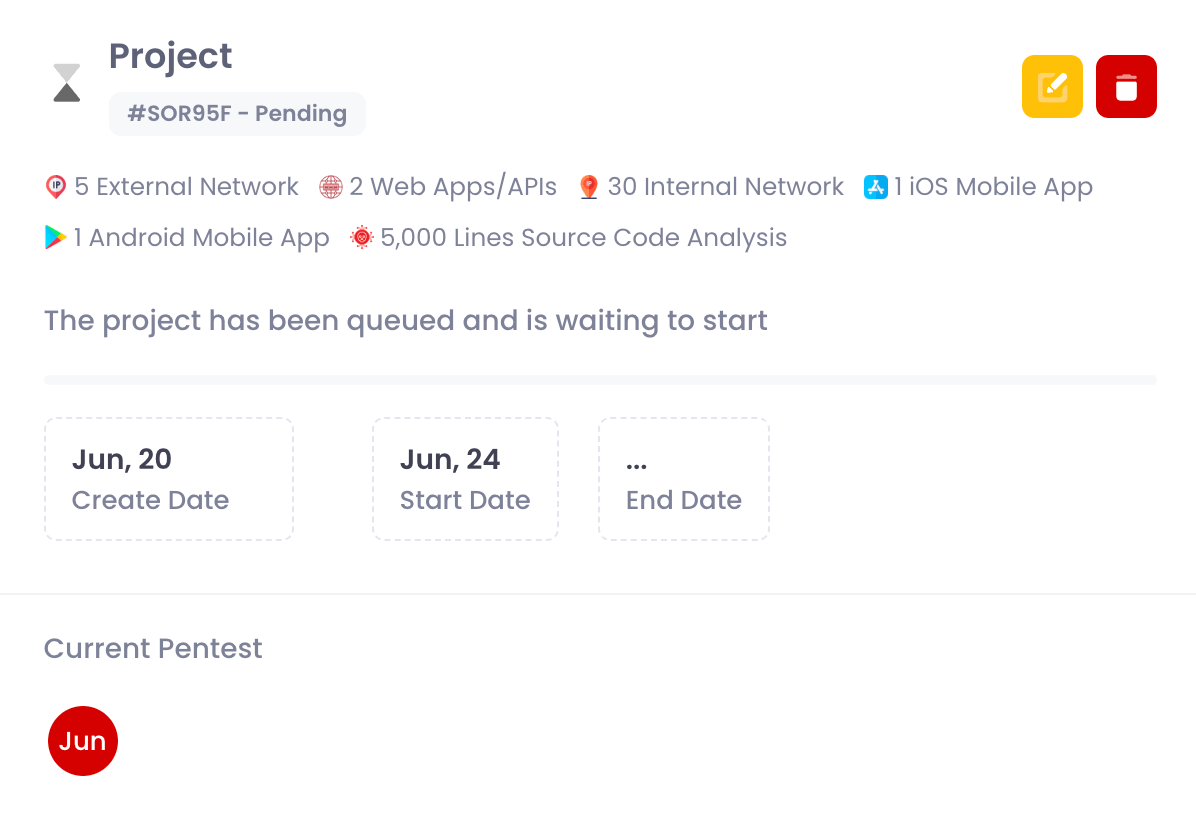
The duration of Penetration Testing varies based on factors such as the size and complexity of the target environment. It can range from a few days to several weeks.
Enfoa allows you to schedule recurring tests at predetermined intervals, ensuring continuous monitoring of your security posture.
By integrating Penetration Testing into the software development lifecycle, Enfoa can help identify vulnerabilities early, leading to more secure code and faster remediation.
Yes, Enfoa conducts tests controlled and safely to minimize or no disruption to your systems.
Enfoa allows you to export and share reports in various formats (such as PDF, Excel, CSV, XML, JSON) for collaboration, auditing, or compliance purposes.
You can download your report from Enfoa’s secure app after logging in with two-factor authentication and choosing PDF, Excel, CSV, XML, or JSON formats.



