Fake GitHub Accounts Used by Hackers for Malware Spread
A threat actor, by the name of Stargazer Goblin, used a wide-reaching DaaS scheme with more than 3,000 fake GitHub accounts in a very organized manner to spread all types of information-stealing malware, resulting in $100,000 of illegal profit in just one year. The enormous network Check Point is calling the “Stargazers Ghost Network” is made up of thousands of repositories that are used to share malicious links and malware. The families—Atlantida Stealer, Rhadamanthys, RisePro, Lumma Stealer, RedLine—are part of the network’s malware portfolio.
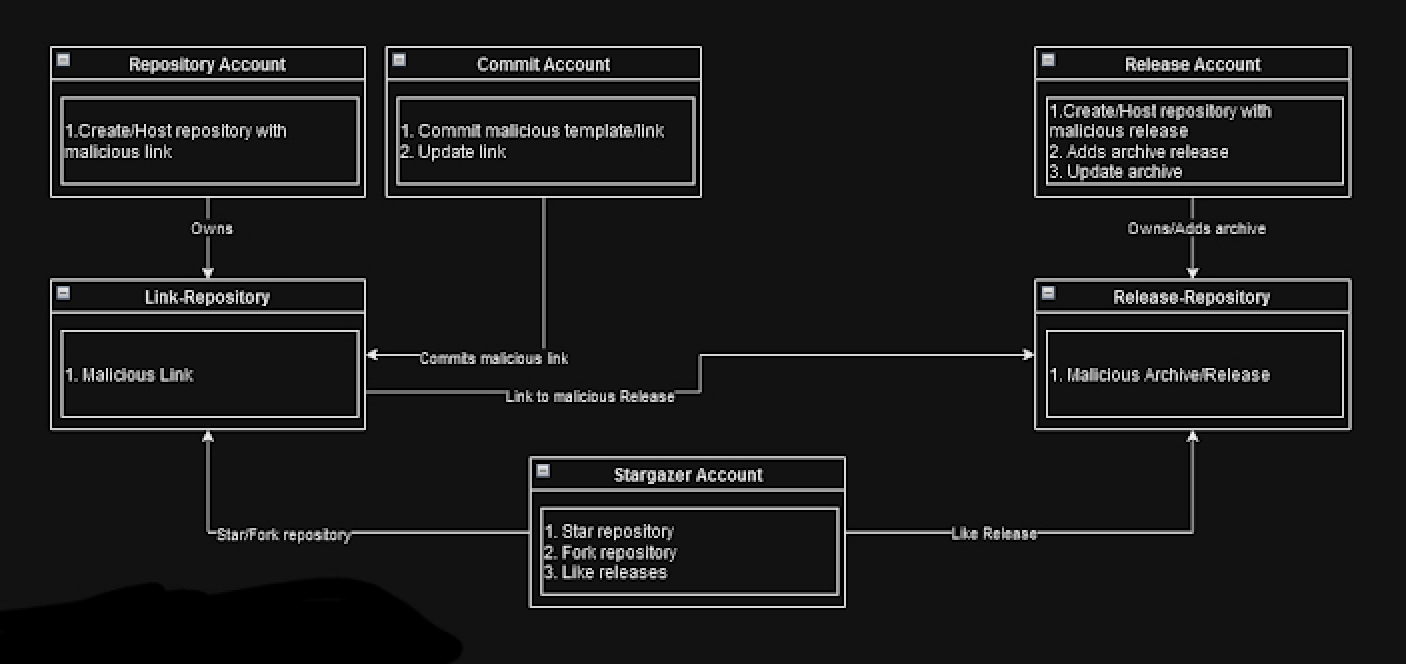
The fake accounts are conducting stars, forks, watching, and subscriptions to malicious repositories among other activities, in an effort to make them look more realistic. The network was active since at least August 2022, while advertisements for the DaaS began to surface from early July 2023. According to security researcher Antonis Terefos, these ‘Ghost’ accounts do not only distribute malware but are constantly active in many other activities so as to resemble a normal user. This adds to the illusion of legitimacy of their actions and the repositories that are associated with them.
Different types of GitHub accounts are used for different functions in the operation, including ones to host the phishing repository template, supply images for it and upload malware to be distributed from password-protected archives masquerading as cracked software and game cheats. As distributing accounts are identified by GitHub and suspended, the operators refresh the phishing repositories with fresh links to live malicious releases, thereby reducing the impact on their campaign. Most of the accounts in this network are compromises to their credentials, most likely acquired through stealer malware. The robustness of the network is supported by its very low proportion of repository and stargazer accounts receiving bans; on the other hand, commit and release accounts are generally banned when detected.
This mechanism updates the links one after the other persistently, keeping it alive despite closures by GitHub. Another of the campaigns was learned to distribute through a malicious link that referred to a GitHub repository. From there, it took victims to a PHP script hosted on a WordPress site and finally delivered the Atlantida Stealer through a PowerShell script. Other malware families such as Lumma Stealer, RedLine Stealer, Rhadamanthys, and RisePro have had propagation by this DaaS. The GitHub accounts are a subset of a much larger DaaS offering, operating with the same ‘Ghost’ accounts across Discord, Facebook, Instagram, X and YouTube.
Stargazer Goblin’s operation is sophisticated enough to keep it under the radar because of the apparent legitimacy that comes with GitHub, in turn substantially minimizing suspicion and allowing a quick recovery from outages. The second operation follows the same tone: that of extortion. The Stargazers Ghost Network began operations in February 2024, and has been targeting GitHub repositories. In the operations, one of the unknown threat actors would wipe the contents of the repository and then ask the victims to contact a user by the name Gitloker, through a Telegram handle, to restore access. This type of attack that involves social engineering was done by emails sent to developers from ‘notifications@github.com,’ luring them to an offer for a job opportunity at GitHub.
Victims are then taken to authorize a new OAuth application that, in turn, destroys their repositories and asks for a ransom to have them restored. Furthermore, Truffle Security has illustrated how an attacker is able to obtain sensitive information from GitHub victims, such as deleted forks, deleted repositories, or even private repositories, and issued a call-to-arms for organizations to protect against what it is calling the Cross Fork Object Reference (CFOR) vulnerability. It exists since one forked repository could access all sensitive data, which are available in commits of a second forked repository. That can be public or deleted. That means, in other words, that all commits of any repository of all forks of the network repository accessible from all repositories of the same network, including from the main upstream repository. This also means, if the upstream repository is a private one, and it became public, all the commits of this and all linked forks become automatically available.