Google Workspace Email Verification Hacked for Account Access
Google has recently made a patch for a security issue in which some malefactors managed to bypass email verification for setting up Google Workspace accounts and thus mimicked the holders of certain domains on unrelated services that support “Sign in with Google.” The users targeted by this operation had received emails from Google, specifying that suspicious Workspace accounts had been blocked.
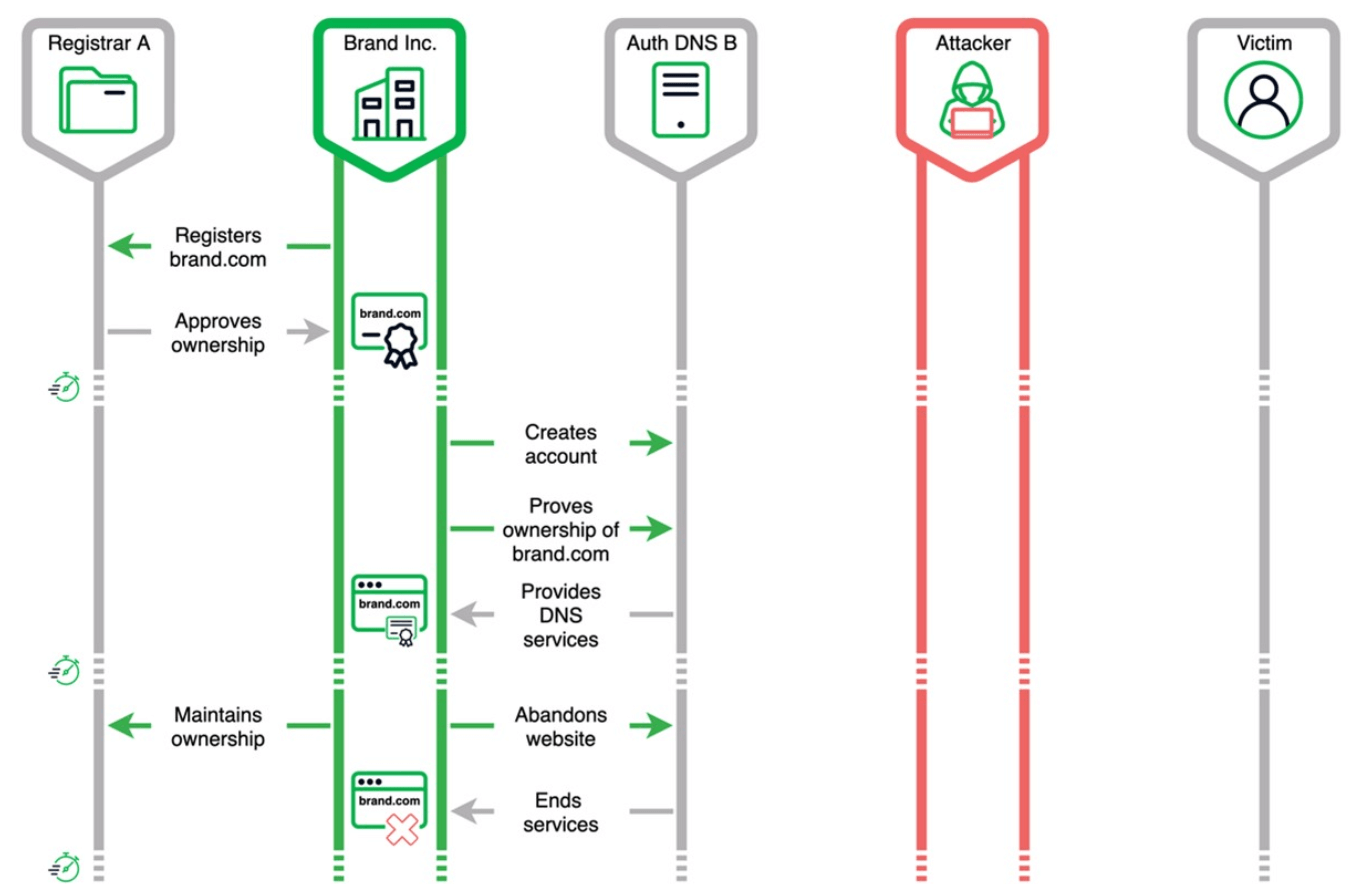
Google uncovered a low-level abuse campaign where attackers were using specifically crafted requests to bypass Google Workspace email verification processes for the accounts. At that point, the attackers could log in to third-party applications under that Google single sign-on service. Google closed the hole within 72 hours of detection and added some additional enforcement to stop similar authentication bypasses.
Google Workspace director of abuse and safety protections Anu Yamunan said that this activity had started in late June and that this involved only a few thousand Workspace accounts which were created without domain verification. While Google Workspace offers a free trial, even for services such as Google Docs, one needs to verify their domain to access Gmail. The attackers attacked a weak link that enabled them to bypass the verification process. Yamunan said that attackers used one email address to sign in and a different email to verify a token, thus providing them access to third-party services.
No malicious Workspace accounts were indeed leveraged in exploiting Google services as part of this security breach. Instead, the attackers used it to perform impersonation of the domain holder on other online services. The authentication bypass eventually permitted the linking of their domain with a Workspace account, which they used to sign in to third-party services.
Google also said the authentication bypass had nothing to do with a recent issue with its cryptocurrency-based domain names, which were compromised during the transition to Squarespace. On July 12, several cryptocurrency-related domains were hijacked from users who hadn’t set up their Squarespace accounts yet. Squarespace explained these as a vulnerability concerning OAuth logins, which they soon patched.