Grandoreiro Malware Resurfaces with Sophisticated Phishing Tactics
And now, it would seem, the Grandoreiro banking Trojan is back once again, targeting Latin American banks. The malware known as “Grandoreiro,” belonging to the Mekotio family, is designed to steal banking access credentials and other confidential information from its victims. What really makes Grandoreiro more alarming than other malware is the usage of advanced techniques in operations such as self-initialization in the infected system for a stealth attack.
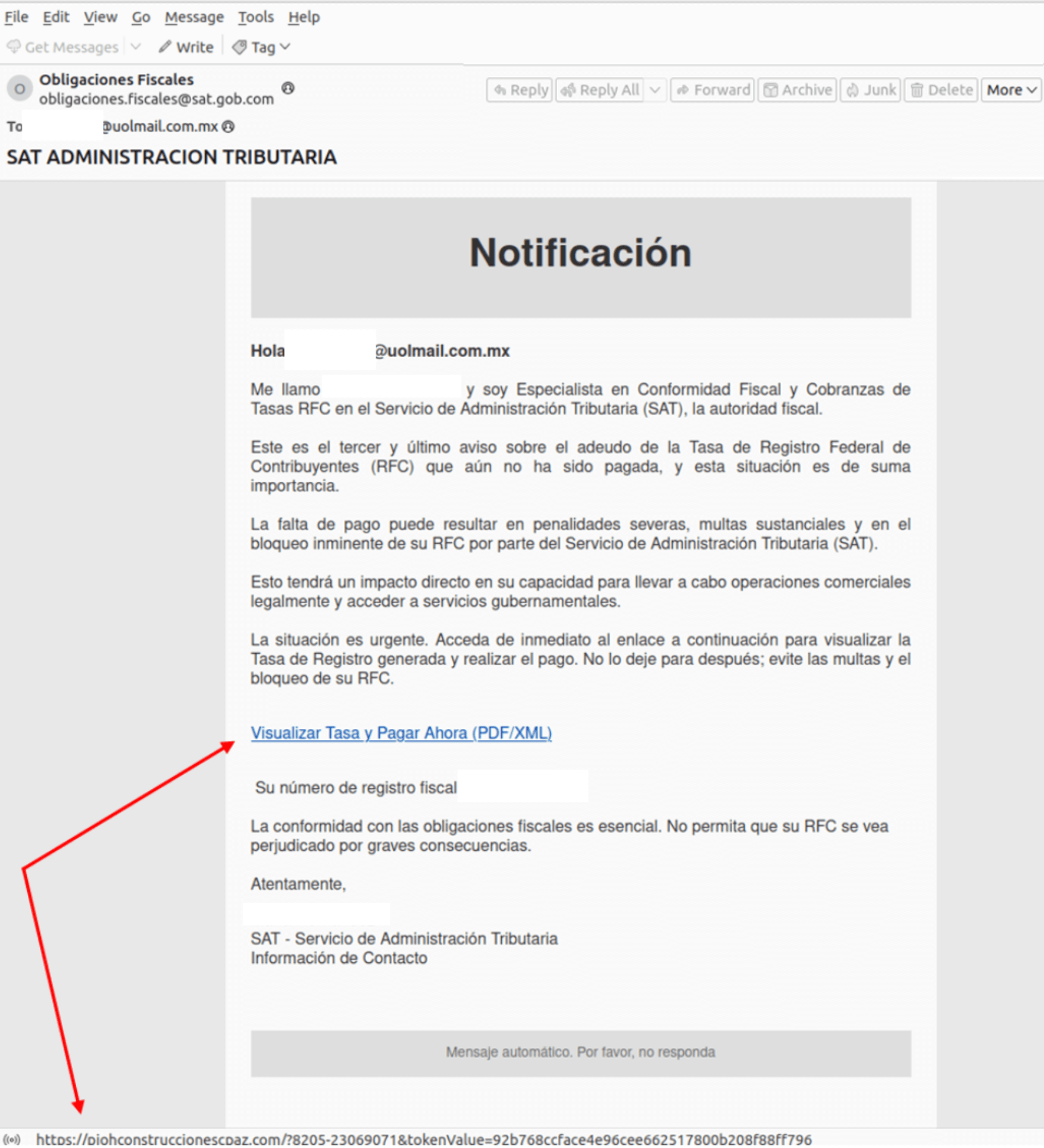
The severe resurgence of Grandoreiro must be attributed to its updated distribution methods. Currently, attackers are using phishing campaigns with malicious attachments and links in order to infect an unsuspecting user. Spam messages are made to appear very convincing at first glance, typically imitating correspondence from financial organizations, in an attempt to fool users into opening the embedded malicious payload or attached file. Once executed, the malware will install and will start capturing user credentials. The information captured will be sent back to the attacker.
A distinct feature of this Trojan is the use of fake pop-up windows, which mirror banking sites. Pop-up windows are displayed while normal banking sessions are in progress, with the user asked to re-enter their login credentials. This makes it more likely that they will be able to capture real login information. Furthermore, the malware includes features to disable security software, thus further guaranteeing its presence on the victim’s device.
The whole evolution of Grandoreiro once again witnesses the cat-and-mouse game between cybercriminals and security professionals. With defenders devising new techniques to detect and mitigate cyber threats, attackers constantly change their behaviors and models, devising new ways to get past the measures of security. This means a security professional has to be eternally watchful, with security software and practices in a state of constant updating.
One needs to be careful while receiving emails, especially unsolicited, from banks or other financial institutions. The legitimacy of this can be verified by direct contact with the institution to not fall prey to these well-crafted sophisticated phishing attacks. Regular training and awareness programs can also make users recognize and avoid potential threats.