Hackers Utilize Cloudflare Tunnels for Stealthy Malware Distribution
Cybersecurity companies have alerted the public of increased exploitation of Cloudflare’s TryCloudflare free service for malware distribution. The activity has been noted by both eSentire and Proofpoint and how attackers make use of TryCloudflare to create a one-off tunnel, making it possible for them to move the traffic flow from their server to a local machine through the Cloudflare infrastructure.
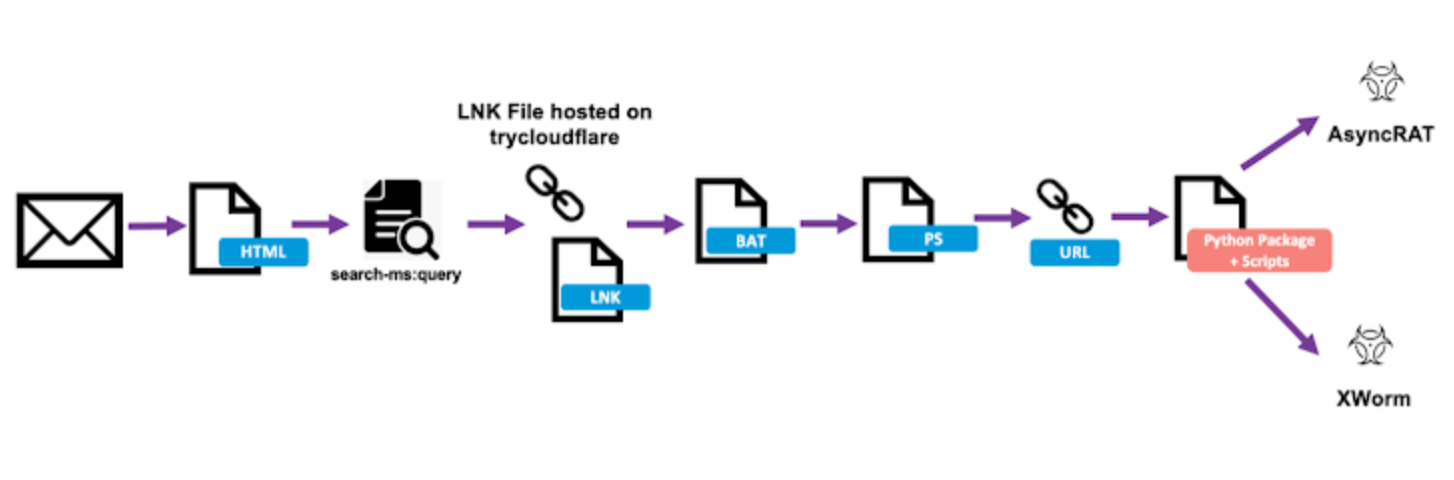
The attack chains using this approach were seen downloading different malware families, among which are AsyncRAT, GuLoader, PureLogs Stealer, Remcos RAT, Venom RAT, and XWorm. Normally, the phishing email is the first component in the chain. It is packed in a ZIP archive and contains a URL shortcut file. The victim’s machine will download a Windows shortcut file from a TryCloudflare-proxied WebDAV server to open the URL shortcut. After being opened, the shortcut file runs batch scripts that download and execute secondary Python payloads; they even open a decoy PDF document, once again from the WebDAV server, in order to keep up appearances. Further, the payload download is made, a decoy PDF gets opened, and file attributes are manipulated for stealth.
What is most notable about this is that they make ample use of direct syscalls to bypass security tools, decrypt multiple layers of shellcode, and employ the Early Bird APC queue injection method for stealth code execution. According to Proofpoint, the phishing lures are in English, French, Spanish, and German. The email volumes range from a few hundred to tens of thousands of emails and are targeted at organizations around the world. The topics of these emails are extremely varied, with subjects covering invoices, documents, package delivery, and taxation.
Although this campaign is related to this cluster, no attribution can be made to any specific threat actor or group. Nevertheless, the campaign appears to have financial motives. The abuse of TryCloudflare for malicious operations was initially seen last summer when Sysdig found a cryptojacking and proxyjacking operation that it named LABRAT. This campaign leveraged a critical vulnerability in GitLab (now patched) to infiltrate targets and obfuscate command-and-control servers using Cloudflare tunnels. The use of WebDAV and Server Message Block (SMB) for the staging and delivery of payloads thus becomes pertinent for organizations if, at all, they should allow access to external file-sharing services only through known, allow-listed servers.
At a higher level, Cloudflare tunnels provide bad actors with temporary infrastructure that enables scaling operations up or down rapidly through the spin-up and tear-down of instances. All of this makes the defender’s life and traditional security approaches, based on the static of blocklists, much more complicated. Cheap and disposable Cloudflare instances provide attackers with an environment in which they can prepare their assaults by using helper scripts, minimizing exposure to detection and takedown efforts. These findings led the Spamhaus Project to demand that Cloudflare reconsider its anti-abuse policies, as cybercriminals increasingly use the services it offers to obscure malicious activity and improve their own operational security with the help of living-off-trusted-services.